Loving the facial recognition feature on your phone? But is it safe? You’d think what could be safer than that? Unfortunately, you’re mistaken facial recognition is not completely safe at all!
Back in 2017, when Apple introduced the feature, Vietnamese security researchers were able to unblock it within minutes with a $150 mask.
Apple improved upon its Face ID feature by employing many security checks such as the use of an infrared camera, depth sensor, and dot projector that maps 30,000 points on your face. This enables the software to create an artificial 3D scan, which makes it secure enough to unlock your phone, but for that, Apple charges a premium price of $999.
Apple’s Face ID vs. the World

Cellphone companies around the world had to obviously get this feature on their products as fast as possible to compete against the industry’s giant and that too at a cheaper rate. This meant a lesser focus on security and hardware.
In 2019 almost every phone offers the facial recognition feature, and this amount is expected to reach 1 billion by 2020. In the race to provide this function many companies like LG, Vivo, Oppo, and the likes rely only on the front camera and some facial recognition algorithms for authentication.
According to Kaspersky Labs, “an inexpensive phone’s facial recognition relies on just the front-facing camera and some not-so-advanced algorithms. But a regular 2D camera without an IR sensor or dot projector can be easily fooled by photos snagged from a social media profile and printed on paper or shown on a screen.”
The chances of someone else’s fingerprint working on your phone are 1 is to 50,000, while with face recognition it goes to 1 is to 1 million. The figure seems immensely convincing that face recognition is the best bet, but that’s not true, at least not for now!
With the use of 3D masks, photographs, and other techniques, like attacking one of the components of the face unlock feature, it is highly possible for someone to access your device.
Cyber security awareness is of utmost importance in this day and age. For example, this year, it is estimated that the VPN services global market is worth $23.60 billion, which indicates that there is a huge market for cyber security.
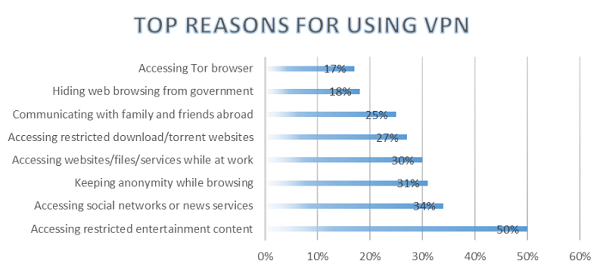
But as we dug deeper, we found that 50% of the VPN users were simply using it to access region-blocked entertainment content rather than for security purposes.
Solution
As companies realize the importance of a secure and strong face unlock feature, many are taking corrective steps to make this feature even more secure.
Recently Vivo mobiles have updated its face unlock tool in an attempt to make it more secure. Similarly, Samsung has combined two security layers by incorporating an iris scanner along with face recognition.
Again the problem with iris scanning is that despite everyone having a unique set of millions of cells, it can still be compromised using a printer and a contact lens. What’s even worse is that your prints can be sold.
OnePlus also plans on introducing technology that would be able to identify real faces by analyzing shadows and bright areas instead of someone using a photo of you.
Until really foolproof face recognition technologies are not developed, it best-advised stick to your fingerprint sensor and a four to six digit PIN.
Word of Caution
The cellphone company cannot be held accountable in case of any loss that you may incur, as the user has consented for weaker security states: Sunil Abraham, executive director at the Centre for Internet and Society.
You may also like to read: 5 Best Ways to Prevent Your Phone from Being Hacked