How Disaster Recovery Planning Protects Your Business From Downtime
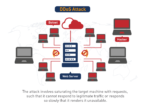
SecurityDisaster recovery for a business is a tricky road. Statistics indicate that nearly half of businesses struggle to reopen after going through a disaster. Now you might be wondering, what does the word disaster mean in this context? A disaster could be as simple as a minor chokehold in the supply chain, a vendor disappearing, which can cause a chain reaction, leading to losing clients, especially if your business is in a competitive market. However, it could also mean major data and security breaches that can lead to permanent infrastructural damage, and the cost of repair can really set a business back financially. The greatest way of avoiding this outcome could simply be devising a Disaster Recovery Plan (DRP) preemptively to counter any blowback. Here are a few ways in which a DRP can protect your business.
How Disaster Recovery Planning Protects Your Business From Downtime Read More »