Do you use an Internet-connected device? If so, the chances are that, at one point or another, you have been the target of a distributed denial-of-service (DDoS) attack.
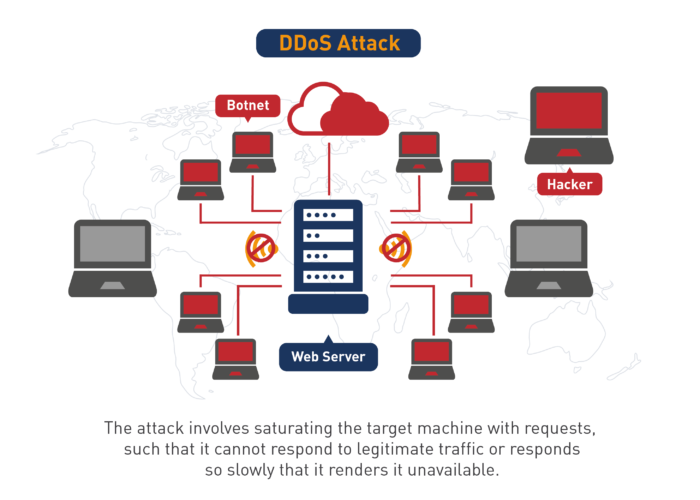
Fortunately, getting DDoS-ed is usually more of a nuisance than a real threat. Nevertheless, you should not underestimate the risks involved. Educating yourself about how DDoS attacks work and how to prevent them is critical for the security of your systems and data.
With that in mind, here are 11 things you should know about DDoS attacks:
1. DDoS Attacks Are on the Rise
According to the Cisco Annual Internet Report (2018–2023), there was a 776% spike in DDoS attacks between 100 and 400 Gbps in the span of just a year from 2018 to 2019. Furthermore, the total number of DDoS attacks globally is expected to grow from 7.9 million in 2018 to a whopping 15.4 million by 2023. That’s all the more reason to stay vigilant and make sure you have adequate cybersecurity measures in place.
2. DDoS Attacks Are Costly
The cost of an average DDoS attack ranges between $20,000 and $40,000 an hour, and some can go all the way up to $50,000. What’s more, that figure can skyrocket depending on the industry: financial institutions, for one, incur losses averaging $18 million per firm as a result of cyberattacks.
3. DDoS Attacks Are Not the Same as DoS Attacks
A denial of service (DoS) attack is a catch-all for many different types of attacks that all aim to disrupt services. These include DDoS, as well as advanced persistent DoS, application layer DoS, and DoS as a service, which many organizations use to stress-test their company networks. In that sense, a DDoS is just one type of DoS attack.
4. There Are Two Main Types of DDoS Attacks
DDoS attacks come in two main categories: bombardment or volumetric attacks and technological infection. Both attack the target network with an overwhelming amount of web traffic with the goal to cause the server to crash and become vulnerable to abuse.
Bombardment
Bombardments are coordinated DDoS attacks originating simultaneously from a number of devices. Hackers typically target poorly protected IoT devices. Such attacks can be both short- and long-term, lasting anywhere from a few seconds to weeks on end. However, most volumetric attacks tend to be rather short.
Technological Infection
Technological infection or Layer 7 attacks often target and manipulate applications and have them do their bidding. IoT devices are particularly vulnerable to such attacks. However, technological infection attacks can also compromise large-scale cloud-based service applications, affecting entire organizations.
5. IoT Devices Are Uniquely Vulnerable to DDoS Attacks
Internet-of-things devices such as home security systems, baby monitors, robot vacuum cleaners, air filters, fitness trackers, and other smart household appliances are particularly vulnerable to DDoS cyberattacks. Rather than being the main target of the attack themselves, unprotected IoT devices often get hijacked and manipulated to send enormous amounts of traffic to the target server.
6. DDoS Attacks Can Be Surprisingly Long
Check this out: the longest DDoS attack in the final quarter of 2018 lasted a record 329 hours or nearly two weeks! The average duration of DDoS attacks was 218 minutes — an impressive rise from the average of a mere 95 minutes for the first quarter of that same year.
7. Monocultures Are a Bad Idea
Automating and replicating the same systems over and over again may be convenient and cost-effective in the short term but makes your organization extremely vulnerable to potential DDoS attacks over time. All it takes for hackers is to identify a single weak link or develop a signal piece of malware to be able to exploit the entire network.
8. You Should Stay Away from Technical Debt
Not following all security practices when building or implementing new software never ends well. Skipping essential development steps may well save you time and money at first, but you are sure to pay a high price later on. Think of an IoT device that has no default password: hackers can easily recruit it into a botnet network for the purposes of launching DDoS attacks.
9. Complex Systems Can Be Less Secure
The more sophisticated a system is, the more challenging it is to operate, monitor, and defend it against cyberattacks. So, unless sophistication is absolutely necessary, it is worth considering opting for a simpler option.
10. DDoS Attacks Can Be Launched for a Variety of Reasons
Many DDoS attacks are carried out for financial motives and often go hand-in-hand with ransomware attacks, where the hacker extorts the victim to pay a fee in exchange for putting an end to the attack. However, a surprising number of DDoS attacks are launched for tactical reasons such as commercial, industrial, and even state-sponsored espionage.
There are ideologically and politically motivated DDoS attacks, too. Protesters, human rights activists, and terrorist organizations alike all use cyberattacks to sabotage governments and state institutions.
11. Knowing What to Watch Out for Is One of the Best Ways to Prevent DDoS Attacks
Learning how to recognize the red flags of a potential DDoS attack is key to keeping unwanted security breaches to a minimum. Some of the most important telltale signs of a DDoS attack include:
- Users — customers as well as employees — complaining of unusually slow or unavailable service
- Slow access to files, whether locally or remotely
- Abnormal and drastic spikes in web traffic
- No Internet connection
- Problems accessing different websites or a long-term inability to load a particular website
- An excessive number of spam emails
- Multiple requests coming in from the same IP address over a short period
- Receiving a 503 Service Unavailable message when no maintenance is being carried out.
However, bear in mind that these symptoms can also be indicative of a number of other problems. Therefore, for an accurate diagnosis, it is always best to have your system checked by a professional.
DDoS Attack image source: www.pngegg.com/en/png-wfpek