
When it comes to taking the necessary steps to protect against cybersecurity threats, whether personally, in a business or both, it’s essential to know what those threats are.
Only by understanding the threats can you really start to develop a plan to protect yourself or your business against them.
One of the most common types of cybersecurity attacks that occurs relates to malware. The following gives an overview of malware and what to know about these potential attacks.
What is a Malware Attack?
Malware attacks mean that a cybercriminal creates malicious software. They then install that software on another device without the person or organization’s knowledge. Once the software is installed on the device or network, the cybercriminal can access personal information for an individual or a business.
Any device or operating system can be susceptible to a malware attack, and one specific type of malware attack called ransomware attacks are one of the fastest-growing cybersecurity threats.
Types of Malware
Malware is a very broad term and it can refer to many different types of more specific threats. Some of the most common types of malware include:
- Viruses: A computer virus is what we most commonly associate with malware, but most malware programs aren’t actually viruses. A virus is something that leads a device to modify host files so that when one file is executed the virus is executed as well. Computer viruses in their simplest form are fairly uncommon at this point, and that’s good for most of us because viruses are the only form of malware that causes an infection of other files. Viruses can be especially hard to recover from.
- Worms: Another long-standing type of malware attack is the worm. The worm attack became popular in the 1990s with the rising popularity of email. The worm is self-replicating, and it can spread even without end-users taking any action. Like viruses, worms are less common now than they once were.
- Trojans: Currently, Trojan horse malware is more popular among cybercriminals than worms. Trojans look like legitimate programs to the point that it’s indiscernible that they aren’t, but they have malicious instructions. For this type of malware to work, the end-user has to take action. One example of a Trojan horse form of malware that goes around is a program that appears to do an anti-virus scan on your device. If you click it and follow the instructions, then you’re the victim of the malware.
Related read: 4 Trojan Horse Malware Attacks Waiting at Your Gates

- Hybrids: As it stands currently, most forms of malware are hybrids. They may bring in elements of traditional malware like worms, and then many will change the operating system so that they can be hidden out of view from any anti-malware protection on a device.
- Ransomware: Ransomware has undoubtedly become one of the most common types of malware. Ransomware takes down everything from governmental organizations and hospitals to large companies. Many of these have elements of Trojans, and when they’re executed they encrypt user files. The encryption process can occur in just a few minutes. Then, the malware can determine how much ransom a victim can afford, and the victim has to pay to unlock their files. In many cases even when the victims of ransomware pay, they still don’t get their files unlocked and unencrypted.
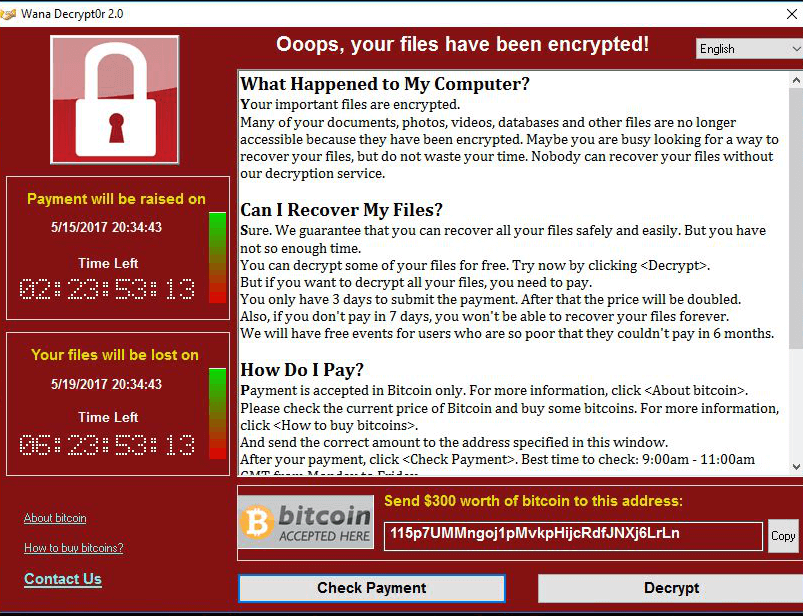
Other Types of Malware
These aren’t the only types of malware. There are other things as well, such as adware and malvertising.
Adware exposes users to malicious forms of advertising—for example, you may be redirected to a fake webpage. Malvertising has similar components—if you click on one of these ads, malware can then be installed on your device.
There is something called wiper malware, and the goal of this type of attack is to take all data and destroy or eliminate it from the targeted device or network.
This might generally be done for one of two reasons. One reason is that the people making the attack have already removed the data they want, or they could just be doing it as a form of sabotage.
Finally, botnets are also malware. Botnet is short for robot network. This refers to a situation where cybercriminals use malware to take over a large network of devices.
This can mean there are a few up to millions of devices affected. It’s not necessarily malware in and of itself, but the networks are created through infections of devices.
Malware is something always changing and evolving, making it important for everyone to pay attention to.
Thanks for sharing great information. Your post is helpful to me…!!