After WordPress, Joomla is the most sought out CMS in the world today. The reason for its popularity is the ease of use and its simplicity. But that does not immune it from the growing vulnerabilities and threats in cyberspace.
Supporting around 1,683,176 websites in the world today, Joomla attracts too many lusting eyes. If not secured properly, a vulnerable Joomla website can end up undergoing a fateful cyber attack, costing money and more.
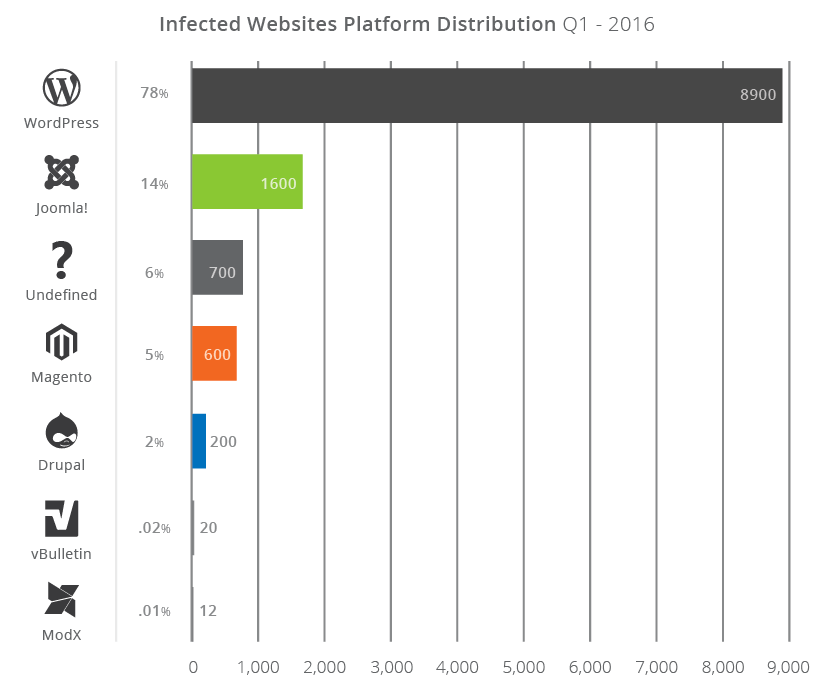
In this article, we have compiled a list of best security practices that you need to include in your Joomla security checklist. But before that, you need to know why it is important for you to take steps in order to secure your Joomla store.
Any eCommerce website is a source of profit for hackers no matter the size of the business. The surprising hacking statistics state that more than 43% of the targeted business are small-scale. Therefore, if you are thinking that your business is not big enough to attract hackers, you might be wrong.
An e-commerce website is generally packed with personal details of customers, plans, and strategies. You do not want the data to fall into wrong hands, do you?
Let’s go through the only security guide that you need for your Joomla store.
Top 8 security practices for your Joomla eCommerce store
Here is the list of the top 8 security practices for your Joomla website.
1. Take regular backups
Almost all the security guides available in the market strongly stresses how important it is to take a backup of your website before performing any task. A regular backup will not only help you when your website is hacked but it will come in handy in case something goes wrong at your end.
There are two main components of a Joomla website: Joomla core files and the database. The process of the backup is also flexible, you can go either for the automated or for the manual process. For more details on the process of backup, look up this blog: 18 best security practices for the Joomla site.
2. Change Joomla database tables prefix
Most of the hackers are aware of the default database prefix. Hence, using the default prefix might not be a good idea. The database of your Joomla store contains information such as your user credentials, site URLs, comments, etc. Henceforth, it would be wise for you to replace the existing prefix with a unique prefix.
Follow these steps to change the database prefix:
- Select Global Configuration from the System menu.

- Now, open the Database Settings by opening the Server Tab.
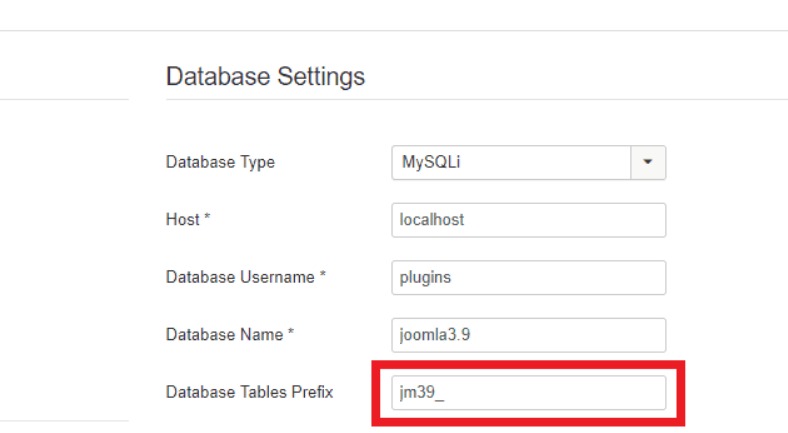
- Now, edit the prefix and add a unique one.
3. Keep your Joomla store up-to-date!
The developers of the Joomla store are known to roll out security patches regularly to safeguard websites from vulnerabilities in the Joomla store. As hackers are generally aware of the vulnerabilities and related security patches, it is important for you to keep the core files of your Joomla store updated at all times. You can get the updated version from the official website of Joomla. The same goes for the themes and extensions. Outdated versions of themes and extensions are a leading cause of cyber attacks on the Joomla store.
4. Enable SEF (Search Engine Friendly)
Enabling the SEF feature will make the URL of your website more search engine friendly with added security benefits. SEF will mask the sensitive information of your website and it will make it difficult for hackers to find security vulnerabilities. Follow these steps to enable SEF in your Joomla store:
- Sign in to the admin account of your Joomla store.
- Go to Global Configuration from the Site.
- Now, select the ‘Yes’ option against the Search Engine Friendly URLs from the Site tab.
- Always keep a tab of ‘Security’ tab in Google webmaster for any issues.
5. Remove inactive and third-party extensions
As an administrator, it is your job to install different extensions and themes to check their functionalities. But an extension from an unreliable third-party source can put your website at risk. Inactive themes and extensions are the most commonly used by a hacker to hide a backdoor. So, verify the source of the extension. And delete all outdated and inactive third-party extensions.
6. Restrict access to the admin area of your Joomla store
The admin area of any website is the most sensitive area. If a hacker gains access to your admin account, it will ruin your website. We suggest restricting access to the admin area as it works most of the time. Follow these steps to restrict access to your website:
- For the first step, create a .htaccess file on your website if not already present.
- Now, add these codes to your .htaccess file:
Order Deny, Allow
Deny from all
Allow from xx.xx.xx.xxIn place of xx.xx.xx, mention the IP address you wish to allow the access.
Here is an alternative, if the above code doesn’t work for your website. Add the following code to your .htaccess file:
RewriteEngine on
RewriteCond %{REQUEST_URI} ^(.*)?administrator$
RewriteCond %{REMOTE_ADDR} !^xx\.xx\.xx\.xx$
RewriteRule ^(.*)$ – [R=403,L]7. Use appropriate file and folder permissions
Another best security step to take is setting the correct file and folder permissions. The default file and folder permissions for Joomla is 644 and 755 respectively. Here’s how you can set secure Joomla file permissions on your store.

8. Two-factor authentication
You must have come across two-factor authentication in popular websites such as Gmail and Facebook where you have to answer a security question in addition to your password to access your account.
Two-factor authentication probably is one of the best (and easiest) methods to protect the admin area of a website. To enable 2FA on your Joomla store, follow these steps:
- Open your admin account.
- Now, go to User Manager >> Edit >> Two-factor authentication.
- And enable the Google Authenticator.
Get professional help!
Aside from the above Joomla security best practices, you must also monitor your website traffic and requests regularly for malware and backdoors. Now, doing all this will be too much effort if you had to do it manually every time. You need not!
There are several security systems available in the market that can automate this process for you. Take for example, a website firewall and malware scanner.
Astra Security is the leading security solution provider for Joomla websites. It provides an efficient security tool that protects your website in real-time and automates the process for you. For penetration testing pricing details, visit Astra’s official website.